The authentication method you use with your portal and whether you allow access to it from outside your firewall affect how you implement a highly available ArcGIS Enterprise.
The following is true for all the scenarios described in this topic:
- The portal machines (p1 and p2 in the diagrams) store content in the same directory, which has been placed on a highly available file server.
- The GIS Server machines (s1 and s2) in the hosting server shares server directories and a configuration store, which have been placed on a highly available file server.
- A highly available relational data store composed of a primary (ds1) machine and a standby (ds2) machine is registered to the hosting server. ArcGIS Data Store has a built-in failover mechanism whereby the standby relational data store becomes the primary data store machine if the primary machine fails. The data store checks the condition of the GIS Server machines for the site with which it is registered, so you can configure the data store through either GIS Server machine URL.
Differences in client/portal communication and authentication protocols are described in the following sections.
Built-in users, clients have access to the portal through ports 80 and 443
In this scenario, portal authentication uses built-in users, and all communication between clients (shown at the top of the diagram) and the portal occurs inside the firewall.
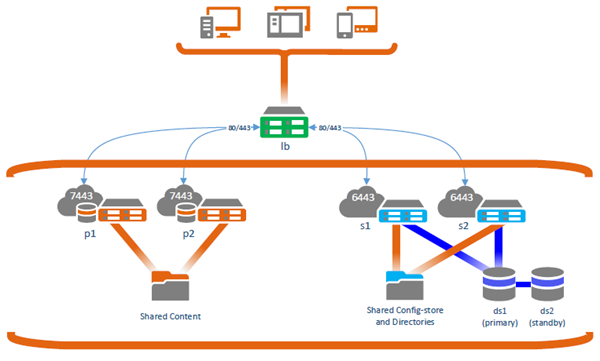
In the example above, clients access the portal website through the load balancer with URL https://<lb>.<domain>.com/<context>/home/, and the ArcGIS Server REST directory can be reached through https://<lb>.<domain>.com/<context>/rest. The highly available portal (two Portal for ArcGIS machines, p1 and p2) communicate with its hosting server—a highly available GIS Server site—through the ArcGIS Server Administrator Directory URL (https://<lb>.<domain>.com/<context>/admin). The machines in the hosting server site (s1 and s2) communicate with the portal through the private portal URL (https://<lb>.<domain>.com/<context>). Both the ArcGIS Server Administrator Directory URL and the private portal URL go through the load balancer (lb) to account for redundancy. If one Portal for ArcGIS machine fails or is inaccessible, the hosting server can still communicate with the remaining portal machine, because the load balancer will direct traffic to the remaining machine. Similarly, if one of the hosting server machines fails or is inaccessible, the load balancer will direct traffic from the portal to the remaining GIS Server machine.
Built-in users with public access to the portal
In this scenario, portal authentication uses built-in users, and at least some clients will access the portal across the firewall. Administrative access from outside the firewall needs to be disabled.
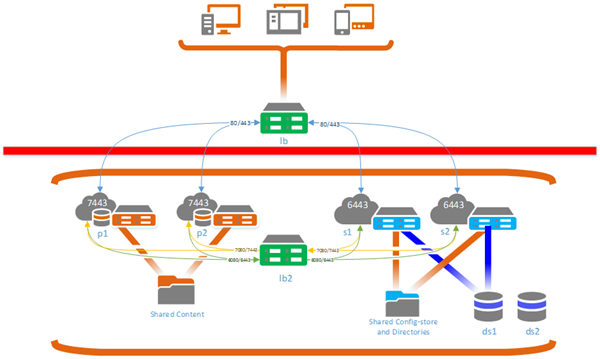
Clients access the portal website and the ArcGIS Server REST endpoint through the load balancer outside the firewall (lb). The portal communicates with the hosting server through the ArcGIS Server Administrator Directory URL, which goes through a second load balancer (lb2) inside the firewall (https://<lb2>.<domain>.com:6443/arcgis, the green lines in the diagram). The hosting server communicates with the portal through the private portal URL, which also goes through lb2 (https://<lb2>.<domain>.com:7443/arcgis, the yellow lines in the diagram) so communication does not have to pass through the firewall. If one portal machine fails, the hosting server can still communicate with the remaining portal machine, as lb2 will send requests to the remaining portal machine. Similarly, if one of the GIS Server machines fails, lb2 will direct traffic from the portal to the remaining GIS Server machine.
Access from clients outside the firewall directly to the GIS Server site will also go through the load balancer outside the firewall (lb).
Administrator access to the ArcGIS Server Administrator Directory and ArcGIS Server Manager are blocked by setting rules on the load balancer outside the firewall (lb).
IWA or LDAP authentication with client access internal
In this scenario, portal users authenticate using integrated Windows authentication (IWA) or lightweight directory access protocol (LDAP) authentication, and all clients accessing the portal are inside the firewall.
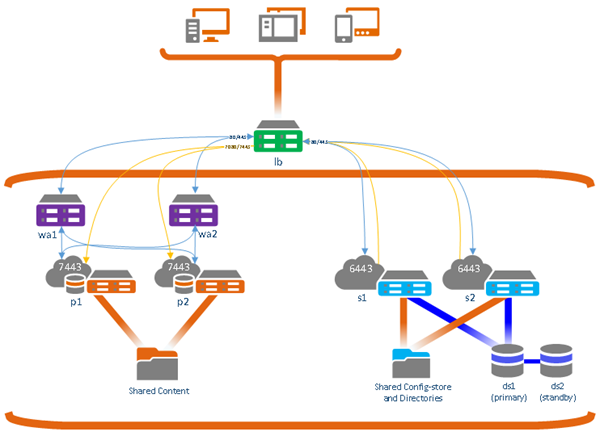
When public access to the portal is not required but clients will authenticate with the portal using IWA or LDAP authentication, each machine in the highly available portal requires a web adaptor (wa1 and wa2). The load balancer (lb) sends traffic to the web adaptors, which then balance requests between the two portal machines (p1 and p2). Any communication from the hosting server to the portal must bypass the authentication challenge at the web tier through the web adaptor. Therefore, the load balancer is configured to listen on ports 7080 and 7443, and that traffic is sent directly to the portal on ports 7080 or 7443 through the private portal URL.
Since public access to the portal is not required, the load balancer can be used for both the public URLs as well as the internal, administrator URLs. The private portal URL is https://<lb>.<domain>.com:7443/arcgis. All other URLs are https://<lb>.<domain>.com/<context>.
SAML or ADFS authentication with public access to the portal
In this scenario, portal users authenticate using Security Assertion Markup Language (SAML) or Active Directory Federation Services (ADFS) authentication, but some clients accessing the portal are outside the firewall. In this case, you need to disable administrator access to the GIS Server machines of the hosting server to secure the services. The following section describes the two configurations to accomplish this.
Note:
Using SAML or ADFS authentication for your portal renders it unnecessary to configure web adaptors with the portal. While you can use ArcGIS Web Adaptor with your portal in the following two scenarios, it adds no functional benefit to the configuration.
Secure a publicly accessed portal using rules set in the load balancer

In this scenario, clients connect through the load balancer (lb) outside the firewall (red line in the diagram), which sends traffic directly to the two portal machines (p1 and p2) on ports 7443 and 7080 and the two GIS Server machines (s1 and s2) on ports 6443 and 6080. Rules within the load balancer block access to the ArcGIS Server Administrator Directory URL and ArcGIS Portal directory.
The load balancer outside the firewall cannot communicate through ports 6080, 6443, 7080, or 7443. Therefore, another load balancer (lb2) is configured inside the firewall to handle communication between the portal and the hosting server. The portal will communicate with the hosting server using the URL defined for the Administration URL during federation (green lines in the diagram) and the hosting server will communicate with the portal through the private portal URL, (yellow lines in the diagram) so communication does not have to pass through the firewall. Lb2 ensures redundancy if one of the GIS Server machines or one of the portal machines fails.
The private portal URL in this scenario is https://<lb2>.<domain>.com:7443/arcgis. The ArcGIS Server Administrator Directory URL is https://<lb2>.<domain>.com:6443/arcgis/admin.
Secure a publicly accessed portal using web adaptors on the GIS Server site
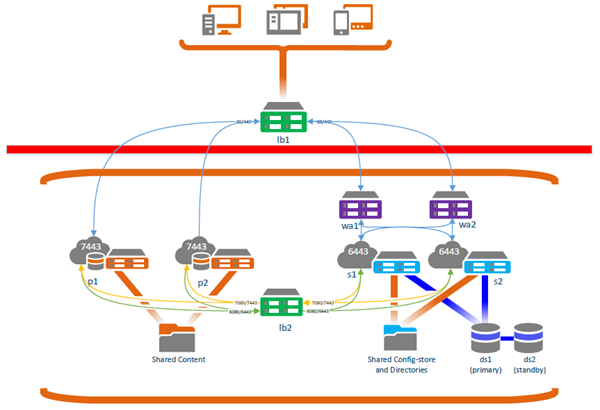
In this scenario, clients connect through the load balancer (lb1) outside the firewall (red line in the diagram), which sends traffic directly to the two portal machines (p1 and p2) on ports 7443 and 7080 and sends traffic to two web adaptors (wa1, wa2) that are configured with the GIS Server machines (s1 and s2). Another load balancer (lb2) handles the traffic between the portal and the portal's hosting server and ensures redundancy if one of the GIS Server machines or one of the portal machines fails.
Clients access the portal through the load balancer (lb1) https://<lb1>.<domain>.com/<context>/home/, which sends traffic to the two portal machines over ports 7080 and 7443. Since the portal is configured with SAML or ADFS authentication, the SAML or ADFS provider authenticates users when they access the portal.
Clients can access the GIS Server site through the load balancer (lb1) outside the firewall, which sends traffic to the GIS Server web adaptors (wa1 and wa2). The web adaptors forward traffic to the GIS Server machines over ports 6080 and 6443.
The GIS Server site communicates with the portal through the private portal URL (https://<lb2>.<domain>.com:7443/arcgis, the yellow lines in the diagram), so communication does not have to pass through the firewall. The GIS Server site is federated to the portal using lb for the services URL. This traffic goes through web adaptors wa1 and wa2, which are configured to block administrator access to ArcGIS Server Manager and the ArcGIS Server Administrator Directory. A second load balancer (lb2) is used for ArcGIS Server Administrator Directory access ( https://<lb2>.<domain>.com:6443/arcgis) to provide redundancy (the green lines in the diagram).